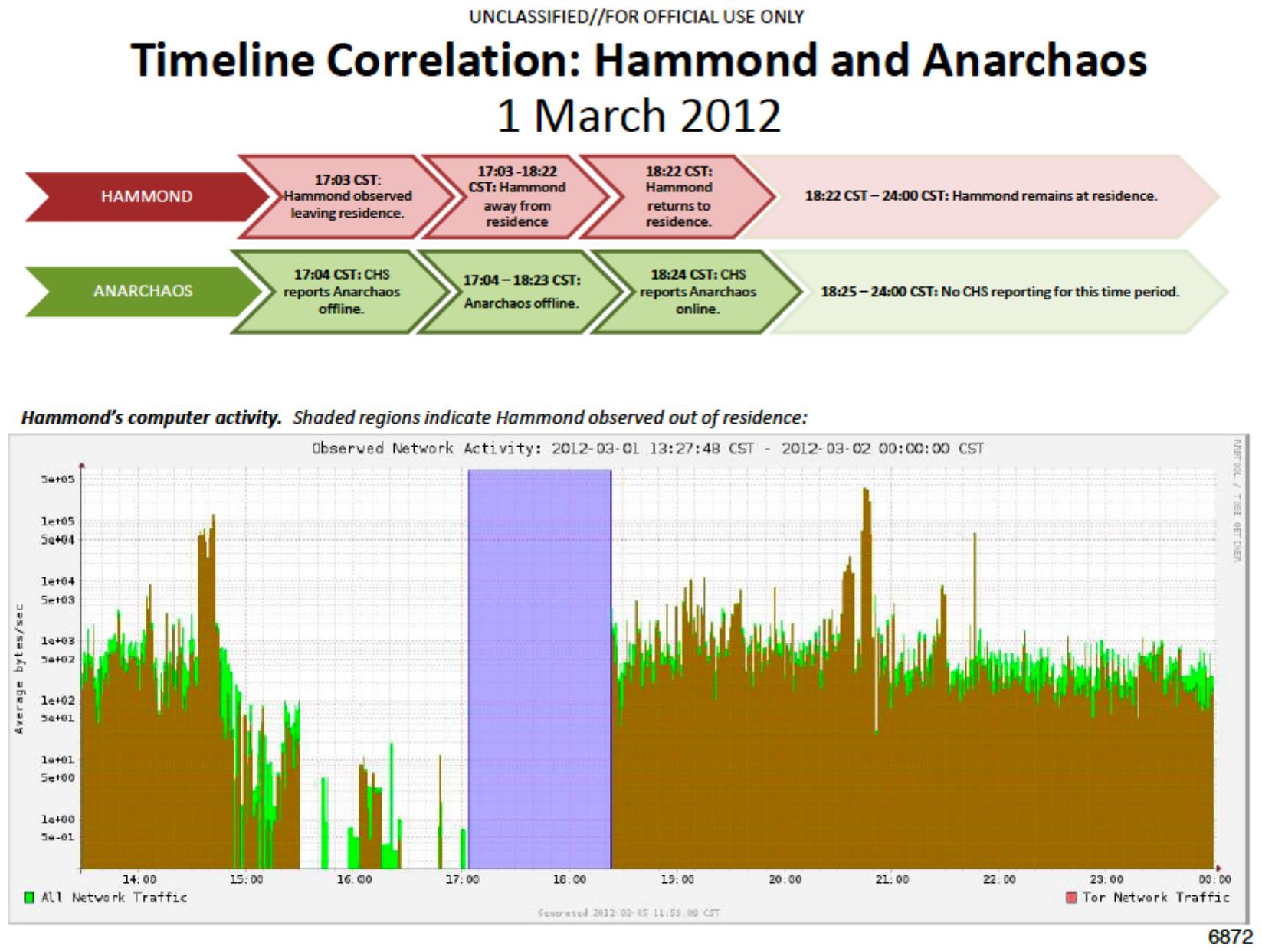
Timeline established by investigators, showing a correlation between the times when Jeremy Hammond was physically present at his home, the times when his online persona (anarchaos) was reported as being online by an informant, and the times when the network traffic of the router he was using showed usage of the Tor network.
In March 2012, Jeremy Hammond's home was raided and he was arrested for his involvement in a December 2011 cyber-attack on Stratfor, a private intelligence firm.[1]
The case was in a large part based on information provided to investigators by Sabu, an associate of Jeremy Hammond who became an informant.
In a 2013 trial, Jeremy Hammond was sentenced to 10 years in prison.[2]
Techniques used
| Name | Description | |
|---|---|---|
| Informants | In June 2011, investigators recruited an associate of Jeremy Hammond, Sabu, as an informant.[1] For several months, Sabu helped investigators build a case against Jeremy Hammond. In exchange for their collaboration Sabu received a lenient sentence: after having spent 7 months in prison (for a bail violation), they were sentenced to time served.[3] Sabu knew Jeremy Hammond's online persona but did not know his real life identity. To find out Jeremy Hammond's real life identity, investigators used information that he had shared with Sabu in online chats, including that:[4]
| |
| Mass surveillance | ||
| Police files | Under his online persona, Jeremy Hammond shared in online chats that he had been arrested at the 2004 Republican National Convention, had spent time in a federal prison and in a county jail, and was currently on probation.[4] Investigators were able to verify all of this using police files, which helped them to link Jeremy Hammond's online persona to his real life identity. | |
| Physical surveillance | ||
| Covert | During a physical surveillance operation against Jeremy Hammond's home that lasted several days, investigators established a correlation between:[4]
| |
| Targeted digital surveillance | ||
| Authentication bypass | Investigators bypassed the authentication of Jeremy Hammond's encrypted laptop, that they had seized in the March 2012 raid.[5] They seemingly achieved the bypass by guessing the laptop's password, which was a very simple password — either “chewy123”[6] or “chewy12345”.[7] | |
| Network forensics | For several days, investigators analyzed the network traffic of the router used by Jeremy Hammond to establish a correlation between:[4]
| |
According to press reports.
According to American Kingpin (Nick Bilton, 2017).

 English
English